No products in the cart.

Introduction
As we move further into 2024, the digital landscape continues to evolve at a rapid pace. With this evolution comes an increasing number of cyber threats that can have devastating effects on businesses of all sizes. IT security has become a critical component of business success, safeguarding valuable data, maintaining customer trust, and ensuring operational continuity. This article explores why investing in robust IT security measures is essential for the long-term success of your business.
Understanding IT Security
What is IT Security?
IT security encompasses the strategies, tools, and processes used to protect digital assets from unauthorized access, attacks, and data breaches. It includes everything from firewalls and virus scanners to encryption and access control measures. Effective IT security ensures that a business’s data, systems, and networks remain secure and operational.
Key Components of IT Security
The key components of IT security include network security, endpoint protection, data encryption, and user authentication. Each of these elements plays a vital role in creating a comprehensive security framework that can withstand the various cyber threats that businesses face today.
The Role of IT Security in Protecting Business Assets
In the digital age, a company’s most valuable assets are often its data and intellectual property. IT security protects these assets from cybercriminals who seek to exploit vulnerabilities for financial gain. By investing in robust security measures, businesses can safeguard their assets and maintain a competitive edge in the marketplace.
The Impact of Cyber Threats on Business Success
Financial Losses from Data Breaches
Data breaches can have significant financial repercussions. Businesses may face hefty fines, legal fees, and the cost of remediation. Additionally, there may be a loss of revenue due to downtime or loss of customers. Investing in IT security is a proactive measure to prevent such costly incidents.
Reputation Damage and Loss of Customer Trust
A data breach can severely damage a company’s reputation, leading to a loss of customer trust. Customers expect their personal and financial information to be secure. When that trust is broken, it can be challenging to rebuild. Effective IT security measures help protect customer data and maintain a positive reputation.
Operational Disruptions and Productivity Losses
Cyberattacks can disrupt business operations, leading to significant productivity losses. Whether it’s a ransomware attack that locks down your systems or a data breach that forces you to shut down operations, the impact on your bottom line can be substantial. Implementing strong IT security protocols helps ensure business continuity.
Common IT Security Threats in 2024
Phishing Attacks
Phishing attacks are one of the most common cyber threats businesses face today. Cybercriminals use deceptive emails or messages to trick employees into revealing sensitive information or downloading malicious software. Educating employees about the dangers of phishing and implementing strong IT security measures can help mitigate this threat.
Ransomware
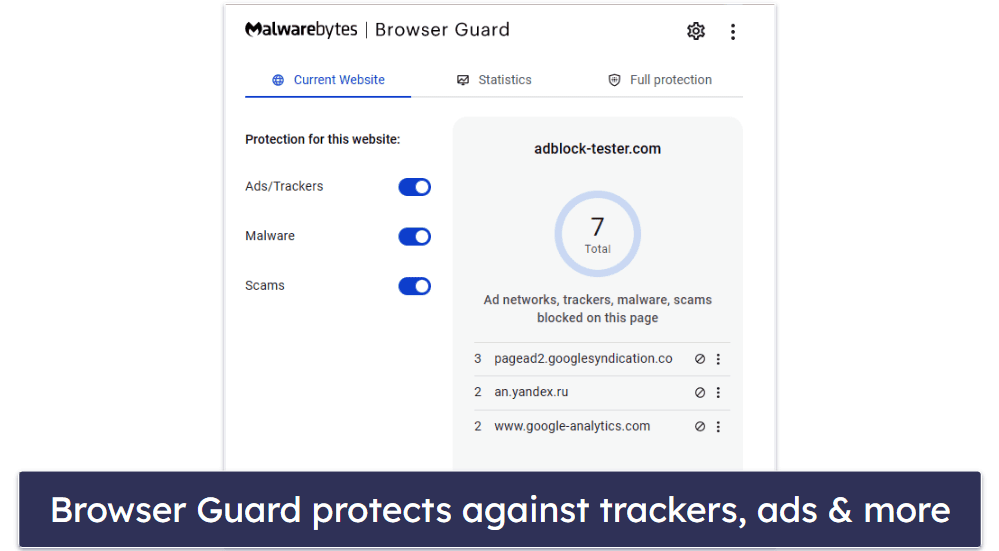
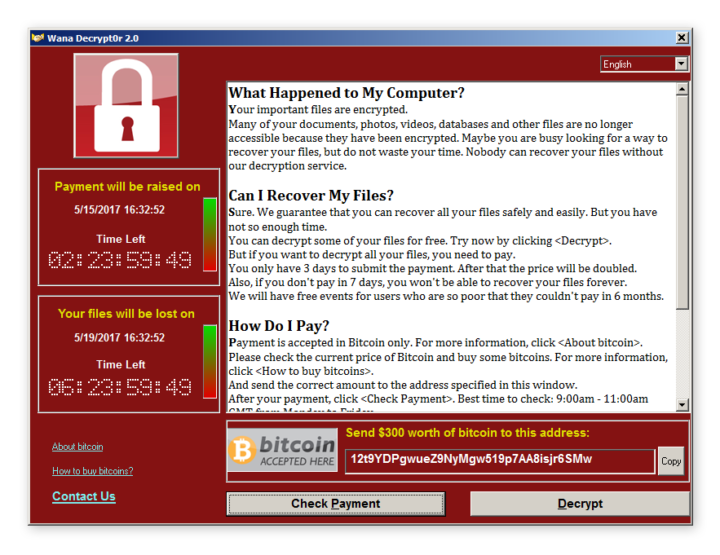
Ransomware attacks involve malicious software that encrypts a company’s data, with the attacker demanding a ransom for its release. These attacks can be devastating, leading to significant financial losses and operational downtime. Using a reliable virus scanner like Malwarebytes is essential for detecting and preventing ransomware.
Insider Threats
Insider threats come from within the organization, often from employees or contractors who have access to sensitive data. These threats can be intentional or accidental, but they can be just as damaging as external attacks. Implementing strict access controls and monitoring for unusual activity are critical components of IT security that help mitigate insider threats.
Advanced Persistent Threats (APTs)
Advanced Persistent Threats (APTs) are prolonged and targeted cyberattacks aimed at stealing sensitive information over time. APTs are often difficult to detect because they operate stealthily within a network. Regularly updating security software and conducting thorough security assessments are essential to defend against APTs.
Why IT Security is Essential for Business Continuity
The Role of IT Security in Disaster Recovery
IT security is a critical component of any disaster recovery plan. In the event of a cyberattack, having robust security measures in place ensures that you can quickly recover your data and resume normal operations. Backup solutions, data loss prevention strategies, and incident response plans are all essential elements of an effective disaster recovery plan.
Ensuring Data Integrity and Availability
Ensuring that your data remains accurate, complete, and available is vital for business success. IT security measures like encryption, access controls, and continuous monitoring help protect your data from unauthorized access and ensure that it is always available when needed.
Protecting Against Data Loss with Backup Solutions
Data loss can occur for various reasons, including cyberattacks, hardware failures, or human error. Implementing robust backup solutions as part of your IT security strategy ensures that you can quickly restore lost data and minimize downtime, thus protecting your business from significant disruptions.
Regulatory Compliance and IT Security
Understanding Key Regulations (GDPR, CCPA, HIPAA, etc.)
Many industries are subject to strict regulations regarding data protection, such as GDPR, CCPA, and HIPAA. Compliance with these regulations is essential to avoid hefty fines and legal repercussions. IT security plays a critical role in helping businesses meet these regulatory requirements by ensuring that data is protected and securely managed.
The Cost of Non-Compliance
Failing to comply with data protection regulations can result in significant financial penalties, legal actions, and damage to your business’s reputation. Investing in comprehensive IT security measures helps ensure that your business remains compliant with relevant laws and regulations, thereby avoiding these costly consequences.
How IT Security Helps Achieve Compliance
IT security measures such as data encryption, access controls, and regular security audits are essential for achieving compliance with regulatory requirements. By implementing these measures, you can protect sensitive data, meet legal obligations, and maintain the trust of your customers and stakeholders.
The Role of IT Security in Building Customer Trust
Protecting Customer Data
Customers entrust businesses with their personal and financial information, expecting it to be kept safe. IT security measures help protect this data from cybercriminals and unauthorized access, ensuring that customer information remains secure. By prioritizing security, businesses can build and maintain strong relationships with their customers.
Enhancing Customer Experience Through Secure Transactions
A secure transaction process is a key component of a positive customer experience. IT security measures such as encryption and secure payment gateways ensure that customer transactions are protected from fraud and other cyber threats. This not only enhances the customer experience but also helps build trust and loyalty.
The Long-Term Benefits of a Strong Security Posture
A strong IT security posture offers long-term benefits for businesses, including increased customer trust, improved reputation, and reduced risk of cyberattacks. By investing in robust security measures, businesses can position themselves as trustworthy and reliable partners in the digital marketplace.
Choosing the Right IT Security Tools for Your Business
Overview of Essential IT Security Tools
A comprehensive IT security strategy requires a combination of tools, including firewalls, antivirus software, encryption, and intrusion detection systems. These tools work together to protect your business from a wide range of cyber threats.
Why Malwarebytes is a Top Choice for Businesses
Malwarebytes is a leading antivirus solution known for its ability to detect and remove malware, ransomware, and other cyber threats. It offers real-time protection, advanced threat detection, and a user-friendly interface, making it an excellent choice for businesses looking to enhance their IT security posture.
Comparing IT Security Solutions
When choosing IT security tools for your business, it’s important to compare features, effectiveness, and ease of use. While Malwarebytes is a top contender, other solutions may offer specific features that better suit your business needs. Conducting thorough research and considering factors such as detection rates, system impact, and customer support can help you make an informed decision.
The Importance of Employee Training in IT Security
Raising Cybersecurity Awareness Among Employees
Employees are often the first line of defense against cyber threats. Regular training programs that raise awareness about common threats, such as phishing and social engineering, are essential for building a strong security culture within your organization.
Regular Security Training Programs
Regular security training programs ensure that employees stay up-to-date on the latest threats and best practices. These programs should be tailored to the specific needs of your business and include practical exercises, such as recognizing phishing emails and responding to security incidents.
Simulated Attacks for Employee Preparedness
Simulated attacks, such as phishing simulations, are an effective way to test employee preparedness and reinforce the importance of vigilance in cybersecurity. By conducting these simulations regularly, businesses can identify areas for improvement and ensure that their employees are ready to respond to real-world threats.
The Role of Cyber Security Online Programs in IT Security
Continuous Monitoring and Threat Detection
Cyber security online programs provide continuous monitoring and threat detection capabilities that are essential for maintaining a secure IT environment. These programs use advanced algorithms to identify and respond to potential threats in real-time, ensuring that your business is always protected.
Integrating Online Programs with Existing IT Security Infrastructure
Integrating cyber security online programs with your existing IT security infrastructure can enhance your overall security posture. These programs work alongside traditional security measures, such as firewalls and antivirus software, to provide a multi-layered defense against cyber threats.
The Future of Cyber Security Online Programs
As cyber threats continue to evolve, cyber security online programs will play an increasingly important role in IT security. Advances in artificial intelligence and machine learning are expected to drive the development of more sophisticated and effective online security tools in the coming years.
Best Practices for Enhancing IT Security in 2024
Regular Security Audits and Assessments
Conducting regular security audits and assessments is essential for identifying vulnerabilities in your IT security infrastructure. These assessments help you stay ahead of potential threats and ensure that your security measures are up-to-date and effective.
Implementing Strong Access Control Measures
Implementing strong access control measures is a fundamental aspect of IT security. By limiting access to sensitive data and systems to only those who need it, businesses can reduce the risk of unauthorized access and data breaches.
Keeping Software and Virus Checker Updated
Regularly updating your security software and virus checker is essential for protecting your business from the latest threats. Updates often include critical patches and new virus definitions that help your tools detect and remove the latest malware.
The Future of IT Security
Emerging Technologies in IT Security
Emerging technologies, such as artificial intelligence and quantum computing, are set to revolutionize IT security. AI-driven security tools can analyze vast amounts of data in real-time, identifying patterns and anomalies that may indicate a security threat. Quantum computing, while still in its early stages, has the potential to break traditional encryption methods, necessitating the development of new security protocols.
Predictive Analytics and AI in Cybersecurity
Predictive analytics and AI are becoming increasingly important in IT security. By analyzing historical data and identifying patterns, these technologies can predict and prevent potential security incidents before they occur. Businesses that invest in these technologies will be better equipped to stay ahead of emerging threats.
Preparing for Future Cyber Threats
As cyber threats continue to evolve, businesses must be proactive in their approach to IT security. This includes staying informed about the latest threats, investing in advanced security technologies, and continuously improving security practices. By doing so, businesses can protect themselves from future threats and ensure long-term success.
Conclusion
In 2024, IT security is not just a technical requirement but a critical factor in business success. From protecting valuable data to ensuring compliance with regulations, robust IT security measures are essential for safeguarding your business against the ever-growing threat of cyberattacks. By investing in comprehensive security solutions, businesses can protect their assets, maintain customer trust, and ensure long-term success in the digital age.
FAQs
What are the most common IT security threats in 2024?
The most common IT security threats in 2024 include phishing attacks, ransomware, insider threats, and advanced persistent threats (APTs). These threats can have significant financial and operational impacts on businesses.
How does IT security impact customer trust?
IT security plays a crucial role in maintaining customer trust by protecting sensitive customer data from cybercriminals. A strong security posture ensures that customers feel confident in doing business with you.
Why is Malwarebytes recommended for business IT security?
Malwarebytes is recommended for business IT security because of its ability to detect and remove a wide range of malware, including advanced threats like ransomware. Its real-time protection and user-friendly interface make it an excellent choice for businesses.
What role does IT security play in regulatory compliance?
IT security is essential for achieving compliance with data protection regulations such as GDPR, CCPA, and HIPAA. Security measures like data encryption, access controls, and regular audits help businesses meet regulatory requirements.
How can businesses stay ahead of emerging cyber threats?
To stay ahead of emerging cyber threats, businesses should invest in advanced IT security technologies, conduct regular security assessments, and continuously update their security practices. Staying informed about the latest threats and trends is also crucial.